Intercept Related Information
William Wong (Talk | contribs) (Created page with "The call data (known as Intercept Related Information or IRI in Europe and Call Data or CD in the US) consists of information about the targeted communications, including dest...") |
William Wong (Talk | contribs) |
||
| Line 1: | Line 1: | ||
| − | The call data (known as Intercept Related Information or IRI in Europe and Call Data or CD in the US) consists of information about the targeted communications, including destination of a voice call (e.g., called party’s telephone number), source of a call (caller’s phone number), time of the call, duration, etc. | + | The call data (known as Intercept Related Information or [[IRI]] in Europe and Call Data or CD in the US) consists of information about the targeted communications, including destination of a voice call (e.g., called party’s telephone number), source of a call (caller’s phone number), time of the call, duration, etc. |
| − | + | ||
| + | ==IRI Records== | ||
| + | |||
| + | * Lawful Interception, a feature as provided by service providers to law enforcement agencies, allows law enforcement agencies to intercept calls | ||
| + | ** By receiving a copy of the audio of both parties | ||
| + | ** By receiving call information records (or IRI records) | ||
| + | * Intercept Related Information Record (IRI record) is�a CDR-style record that contain IRI information on an intercepted call | ||
| − | |||
[[Image:Lawful-intercept-details.png|thumb|360px|Schematic showing interception of a call already routed with a Tmedia]] | [[Image:Lawful-intercept-details.png|thumb|360px|Schematic showing interception of a call already routed with a Tmedia]] | ||
Revision as of 04:43, 21 September 2016
The call data (known as Intercept Related Information or IRI in Europe and Call Data or CD in the US) consists of information about the targeted communications, including destination of a voice call (e.g., called party’s telephone number), source of a call (caller’s phone number), time of the call, duration, etc.
Contents |
IRI Records
- Lawful Interception, a feature as provided by service providers to law enforcement agencies, allows law enforcement agencies to intercept calls
- By receiving a copy of the audio of both parties
- By receiving call information records (or IRI records)
- Intercept Related Information Record (IRI record) is�a CDR-style record that contain IRI information on an intercepted call
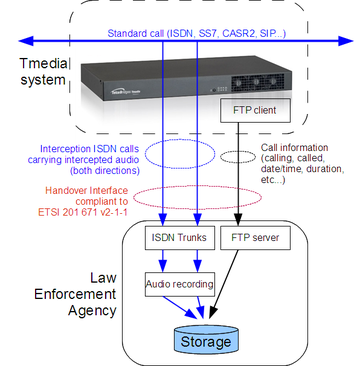
Lawful interception will identify a call to intercept, and send the following information to one or multiple Law Enforcement agencies:
- information on an intercepted call (calling/called numbers, timestamps, call duration, etc.)
- audio from both directions of the call
Interception of a call is triggered by:
- A phone number to monitor
- A date/time period
A call that matches the number and the time period will be intercepted.
Toolpack Implementation
With a Tmedia system running the Toolpack software (version 2.7 or above), lawful interception is triggered by a routing script. This script uses the information from a configuration file (csv format), to determine which phone number must be intercepted during which time period.
A call that matches the number (calling or called number) and the time period will be intercepted.
During the interception, two outgoing calls toward an interception NAP will be placed, each containing a copy of the audio of one direction of the intercepted call. The specified NAP must be configured to point to the Law Enforcement Agency, generally using ISDN trunks.
In addition, information records (containing general call information like calling/called number, timestamps, and call duration, etc., this information is called Intercept Related Information (IRI) records) will be sent to the Law Enforcement Agency. That information is sent as data files (format specified by ETSI 201 671 v2-1-1) to a FTP server (Toolpack also supports SFTP for more security).
Lawful Intercept configuration (NAP to use, login information of the FTP/SFTP server, target numbers to intercept, etc.) can be configured in the Toolpack Web Portal.
H.248 Implementation
Lawful Interception is also supported using H.248 interface.