Upgrade CentOS
Nicole Tan (Talk | contribs) (initial page) |
Nicole Tan (Talk | contribs) (NT: Correction about the Centos7 version) |
||
| (27 intermediate revisions by 5 users not shown) | |||
| Line 1: | Line 1: | ||
| − | {{DISPLAYTITLE: Upgrade CentOS | + | {{DISPLAYTITLE: Upgrade CentOS software packages}} |
| − | + | __FORCETOC__ | |
| − | = | + | == Benefits == |
| + | * Obtain the CentOS security updates | ||
* Patch recent vulnerabilities | * Patch recent vulnerabilities | ||
* Patch SNMP core files | * Patch SNMP core files | ||
| − | = Applicable Products | + | == Applicable Products == |
| − | * TMG800, TMG3200, TMG7800-CTRL | + | * TMG800, TMG3200, TMG7800-CTRL, TSBC, FreeSBC |
| − | * Tdev Linux server | + | * TSG800, TSG3200 |
| + | * Tdev Linux server (CentOS or RedHat) running Toolpack software | ||
| − | = | + | == TelcoBridges repository == |
| − | The | + | The operating system (CentOS) software upgrade is performed using ''yum'' software package manager. The repositories sites providing RPM packages are configured from /etc/yum.repos.d/. TelcoBridges provides a modified CentOS repository copy (http://repo.telcobridges.com) of the official CentOS repository. |
| − | + | If the '''unit or Linux server does not have access to Internet''' (or does not have DNS configured), you should configure an offline CentOS repository on your local machine as explained in the section bellow. | |
| − | + | ||
| − | = | + | === Offline repository configuration === |
| − | + | First, SSH to your unit do determine which version of the OS your system is using: | |
| + | # cat /etc/redhat-release | ||
| + | '''CentOS release 5'''.11 (Final) | ||
| − | + | * [[Configure_Offline_Repository_CentOS5_A|Configure a local offline Repository for CentOS5]] | |
| − | * | + | |
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | '''CentOS Linux release 7'''(Core) | |
| + | * [[Configure_Offline_Repository_CentOS7_A|Configure a local offline Repository for CentOS7]] | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | === | + | == CentOS software packages update == |
| + | The operator can use one of the two methods available: GUI/WebPortal or command line interface. | ||
| + | |||
| + | === WebPortal === | ||
| + | <span style="color:#e68a00"> | ||
| + | '''NOTE''': The GUI/WebPortal CentOS packages software upgrade shown below is only offered on ''T''sbc, ''T''media and ''T''sig product. Tdev Linux server with Toolpack must be upgraded using the Command Line procedure. | ||
| + | </span> | ||
| − | + | To upgrade CentOS software packages, follow this procedure from the web interface of the unit: | |
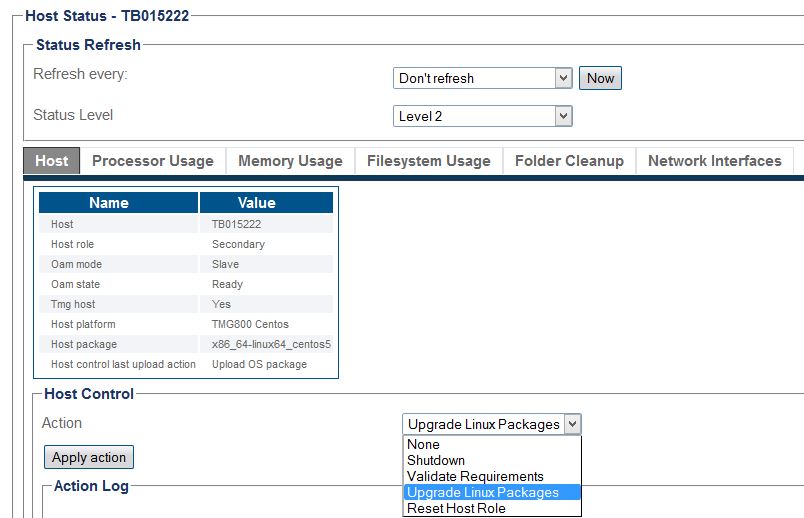
| − | + | * Hosts -> Status -> TBxxxxxx -> Action -> Upgrade Linux Packages, then 'Apply Action': | |
| − | + | [[Image:Upgrade_Linux_Packages.jpg]] | |
| − | * | + | |
| − | + | ||
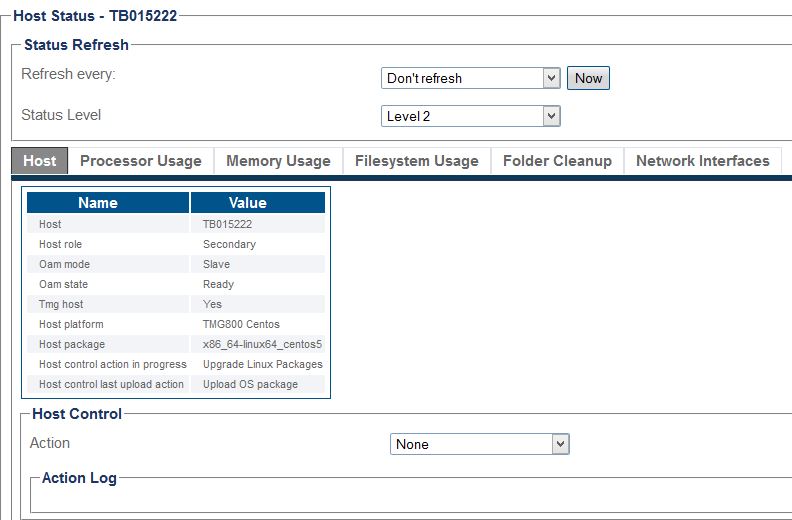
| − | + | When the upgrade is in progress, there is no status shown, and you will see the screen like this: | |
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | [[Image:Upgrade_Linux_Progress.jpg]] | |
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
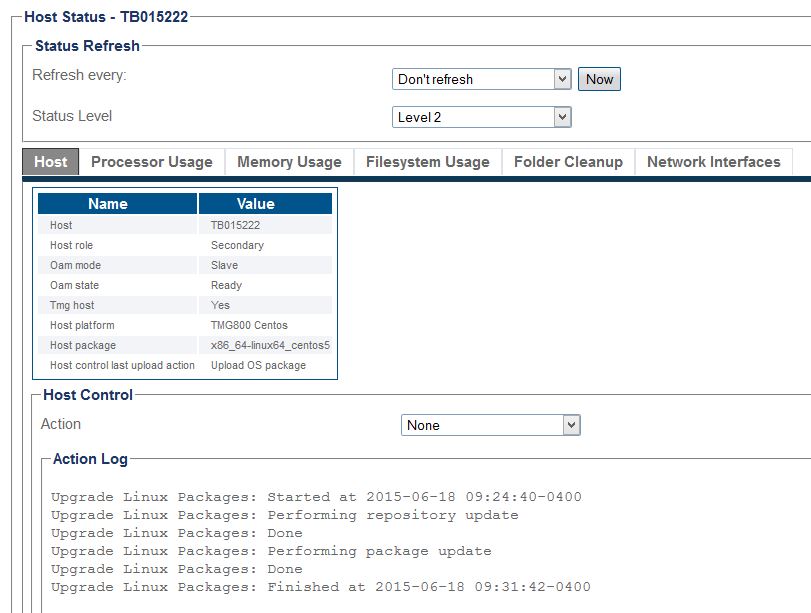
| + | It may take a while 8-10 mins. You need to refresh the page until you see this: | ||
| − | + | [[Image:Centos_Upgrade_Complete.jpg]] | |
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | Once complete, you need to reboot the host: | |
| + | Hosts -> Status -> TBxxxxxx -> Action -> Shutdown -> Reboot | ||
| + | === Command line === | ||
| + | Alternatively, you can ssh to the unit and run the following command: | ||
| + | # yum clean all | ||
| + | # yum update | ||
| − | + | Reboot the unit | |
| − | + | # reboot | |
| − | + | ||
| − | + | ||
Latest revision as of 12:20, 17 April 2020
Contents |
Benefits
- Obtain the CentOS security updates
- Patch recent vulnerabilities
- Patch SNMP core files
Applicable Products
- TMG800, TMG3200, TMG7800-CTRL, TSBC, FreeSBC
- TSG800, TSG3200
- Tdev Linux server (CentOS or RedHat) running Toolpack software
TelcoBridges repository
The operating system (CentOS) software upgrade is performed using yum software package manager. The repositories sites providing RPM packages are configured from /etc/yum.repos.d/. TelcoBridges provides a modified CentOS repository copy (http://repo.telcobridges.com) of the official CentOS repository.
If the unit or Linux server does not have access to Internet (or does not have DNS configured), you should configure an offline CentOS repository on your local machine as explained in the section bellow.
Offline repository configuration
First, SSH to your unit do determine which version of the OS your system is using:
# cat /etc/redhat-release
CentOS release 5.11 (Final)
CentOS Linux release 7(Core)
CentOS software packages update
The operator can use one of the two methods available: GUI/WebPortal or command line interface.
WebPortal
NOTE: The GUI/WebPortal CentOS packages software upgrade shown below is only offered on Tsbc, Tmedia and Tsig product. Tdev Linux server with Toolpack must be upgraded using the Command Line procedure.
To upgrade CentOS software packages, follow this procedure from the web interface of the unit:
- Hosts -> Status -> TBxxxxxx -> Action -> Upgrade Linux Packages, then 'Apply Action':
When the upgrade is in progress, there is no status shown, and you will see the screen like this:
It may take a while 8-10 mins. You need to refresh the page until you see this:
Once complete, you need to reboot the host: Hosts -> Status -> TBxxxxxx -> Action -> Shutdown -> Reboot
Command line
Alternatively, you can ssh to the unit and run the following command:
# yum clean all # yum update
Reboot the unit
# reboot