Lawful Interception
William Wong (Talk | contribs) |
(→References) |
||
| (27 intermediate revisions by 3 users not shown) | |||
| Line 1: | Line 1: | ||
| − | + | Lawful intercept is a feature provided by service providers to law enforcement agencies (FBI, Interpol, RCMP, etc.) that allows law enforcement agencies to intercept calls by receiving a copy of the audio of both parties and call information records. | |
==Overview== | ==Overview== | ||
| Line 5: | Line 5: | ||
[[Image:Lawful-intercept-details.png|thumb|360px|Schematic showing interception of a call already routed with a Tmedia]] | [[Image:Lawful-intercept-details.png|thumb|360px|Schematic showing interception of a call already routed with a Tmedia]] | ||
| − | * Lawful Interception (process of intercepting a | + | * Lawful Interception (process of intercepting a conversation) |
| − | * Interception target (someone under investigation by law enforcement agency, and whom the agency wants to intercept calls) | + | * Interception target (someone under investigation by a law enforcement agency, and for whom the agency wants to intercept the calls) |
| − | * Law enforcement agency ( an agency that has, by law, the power to request the interception of calls | + | * Law enforcement agency ( an agency that has, by law, the power to request the interception of calls to or from targets) |
| − | * A law enforcement agency sends | + | * A law enforcement agency sends to the service provider a list of targets to intercept (phone numbers) |
| − | * Service provider configures its | + | * Service provider configures its equipment to intercept the target phone numbers |
| − | * When service provider | + | * When service provider equipment detects a call that involves a target to intercept, it |
** Forwards a copy of call audio (both directions) to the agency through forked calls (Content of Communication link (CC link) - a call toward the agency, carrying intercepted audio) | ** Forwards a copy of call audio (both directions) to the agency through forked calls (Content of Communication link (CC link) - a call toward the agency, carrying intercepted audio) | ||
| − | ** Sends information records ([[IRI]] records) to the agency | + | ** Sends information records ([[IRI]] records) to the agency |
| − | * Telcobridges | + | * The Telcobridges Lawful Interception implementation is based on specification ETSI ES 201 671 v2.1.1 (2001-09), and not CALEA, PCES, and ANSI T1.678 |
==Lawful Interception Requirements== | ==Lawful Interception Requirements== | ||
| Line 21: | Line 21: | ||
*** LIID (Lawful Intercept Identifier, unique identifier assigned to a target by an agency) for the target | *** LIID (Lawful Intercept Identifier, unique identifier assigned to a target by an agency) for the target | ||
*** Phone number of the target | *** Phone number of the target | ||
| − | *** Start | + | *** Start and end dates and times for the interception |
| − | ** Service provider updates targets in its equipment and | + | ** Service provider updates targets in its equipment and equipment detects a matching calling or called number, and activates the interception |
* Intercepting targets | * Intercepting targets | ||
** In a call, each call leg can be an interception target | ** In a call, each call leg can be an interception target | ||
| Line 38: | Line 38: | ||
* For each direction (audio <<from>> and <<to>> the target): | * For each direction (audio <<from>> and <<to>> the target): | ||
** A new outgoing call leg is made, toward the agency | ** A new outgoing call leg is made, toward the agency | ||
| − | ** Audio is << | + | ** Audio is <<forked>> (half-duplex joined) |
* These outgoing call legs are made toward: | * These outgoing call legs are made toward: | ||
** An outgoing NAP explicitly assigned to the agency | ** An outgoing NAP explicitly assigned to the agency | ||
| Line 44: | Line 44: | ||
* Forking does NOT require DSPs | * Forking does NOT require DSPs | ||
* Audio forking is done as soon as possible | * Audio forking is done as soon as possible | ||
| − | ** Immediately for the audio <<from>> the target (this may include even the ring back tone, or may include audio from incoming call during ringing) | + | ** Immediately for the audio <<from>> the target (this may include even the ring back tone, or may include audio from an incoming call during ringing) |
| − | ** Upon joining with | + | ** Upon joining with another active leg for the audio <<to>> the target |
==IRI records== | ==IRI records== | ||
| − | The call data (known as Intercept Related Information or [[IRI]] in Europe and Call Data or CD in the US) consists of information about the targeted communications, including destination of a voice call (e.g., called party’s telephone number), source of a call (caller’s phone number), time of the call, duration, | + | The call data (known as Intercept Related Information or [[IRI]] in Europe and Call Data or CD in the US) consists of information about the targeted communications, including destination of a voice call (e.g., called party’s telephone number), source of a call (caller’s phone number), time of the call, duration, and more. |
| − | Intercept Related Information record (IRI record) is a CDR-style record that | + | Intercept Related Information record (IRI record) is a CDR-style record that contains IRI information on an intercepted call |
===Types of IRI records=== | ===Types of IRI records=== | ||
| − | + | # IRI-BEGIN: Indicates that the interception is starting at first event of the communication attempt, opening the IRI transaction | |
| − | + | # IRI-CONTINUE: Indicates call state change at any time during the communication attempt within the IRI transaction | |
| − | + | # IRI-END: Indicates the end of the interception at the end of the communication attempt, closing the IRI transaction | |
| − | + | # IRI-REPORT: General use for any non-communication related events | |
For information related to an existing communication case, the record types 1 to 3 shall be used. They form an IRI | For information related to an existing communication case, the record types 1 to 3 shall be used. They form an IRI | ||
| − | transaction for each communication case or communication attempt, which corresponds directly | + | transaction for each communication case or communication attempt, which corresponds directly with the communication |
phase (set-up, active or release).<br> | phase (set-up, active or release).<br> | ||
| − | For some packet oriented data services such as GPRS, the first event of a communication attempt | + | For some packet-oriented data services such as GPRS, the first event of a communication attempt is the Packet Data Protocol (PDP) |
| − | context activation or a similar event and an IRI-BEGIN record | + | context activation or a similar event and an IRI-BEGIN record is issued. The end of the communication attempt |
| − | shall be the PDP context deactivation or a similar event and an IRI-END record shall be issued. While a | + | shall be the PDP context deactivation or a similar event and an IRI-END record shall be issued. While a PDP context is |
| − | active, IRI-CONTINUE records | + | active, IRI-CONTINUE records are used for CC relevant IRI data records, IRI-REPORT records otherwise.<br> |
| − | Record type 4 is used for non-communication related subscriber action, like | + | Record type 4 is used for non-communication related subscriber action, like Subscriber Controlled Input (SCI) for |
| − | service activation. For simple cases, it can also be | + | service activation. For simple cases, it can also be used for reporting unsuccessful communication attempts.<br> |
The record type is an explicit part of the record. The 4 record types are defined independently of target communication | The record type is an explicit part of the record. The 4 record types are defined independently of target communication | ||
events. The actual indication of one or several communication events, which caused the generation of an IRI record, is | events. The actual indication of one or several communication events, which caused the generation of an IRI record, is | ||
| − | part of further parameters | + | part of further parameters in the record's information content. Consequently, the record types of the IRI |
transactions are not related to specific messages of the signalling protocols of a communication case, and are therefore | transactions are not related to specific messages of the signalling protocols of a communication case, and are therefore | ||
| − | independent of future enhancements of the intercepted services | + | independent of future enhancements of the intercepted services and of network specific features. Any transport level |
information (i.e. higher-level services) on the target communication-state or other target communication related | information (i.e. higher-level services) on the target communication-state or other target communication related | ||
| − | information is contained | + | information is contained in the information content of the IRI records.<br> |
For some packet oriented data services such as GPRS, if Lawful Interception (LI) is being activated during an already established PDP | For some packet oriented data services such as GPRS, if Lawful Interception (LI) is being activated during an already established PDP | ||
context or similar, an IRI-BEGIN record will mark the start of the interception. If LI is being deactivated during an | context or similar, an IRI-BEGIN record will mark the start of the interception. If LI is being deactivated during an | ||
established PDP context or similar, no IRI-END record will be transmitted. The end of interception can be | established PDP context or similar, no IRI-END record will be transmitted. The end of interception can be | ||
| − | communicated to the LEA | + | communicated to the LEA a Handover Interface Port 1 (HI1)(for Administrative Information); whereas Handover Interface Port 2 (HI2) transports IRI information and Handover Interface Port 3 (HI3) transports Content of Communication information). |
===Typical information found in an IRI record=== | ===Typical information found in an IRI record=== | ||
| Line 102: | Line 102: | ||
* They provide information on the interception, and call state | * They provide information on the interception, and call state | ||
* In a call, each call leg can be an interception target | * In a call, each call leg can be an interception target | ||
| − | * When a leg is an interception target, | + | * When a leg is an interception target, it's intercepted: |
** Audio «from» this leg is forked to a new outgoing call toward the agency | ** Audio «from» this leg is forked to a new outgoing call toward the agency | ||
** Audio «to» this leg is forked to a new outgoing call toward the agency | ** Audio «to» this leg is forked to a new outgoing call toward the agency | ||
| Line 112: | Line 112: | ||
==IRI records encoding== | ==IRI records encoding== | ||
| − | * IRI records are encoded in ASN.1 (a binary encoding standard that is used by IRI records) format | + | * IRI records are encoded in ASN.1 (a binary encoding standard that is used by IRI records) format and using the basic encoding rules (BER). |
* ASN.1 IDs and objects hierarchy for encoding IRI records is provided by ETSI specifications | * ASN.1 IDs and objects hierarchy for encoding IRI records is provided by ETSI specifications | ||
| Line 156: | Line 156: | ||
Ben Yi,450-621-1990 | Ben Yi,450-621-1990 | ||
</pre> | </pre> | ||
| − | * Enable Lawful Interception in | + | *[[Toolpack:Enable Lawful Interception in Routing Script B|Enable Lawful Interception in a Routing Scripts]] ([[Toolpack:Enable Lawful Interception in Routing Script A|For Toolpack 2.7]]) |
| − | ** The <<lawful interception | + | ** The <<lawful interception>> routing script filter is provided with toolpack |
** Users only need to <<include>> it in their current routing script<br> | ** Users only need to <<include>> it in their current routing script<br> | ||
<pre> | <pre> | ||
| Line 166: | Line 166: | ||
after_filter :method => :enable_lawful_intercept | after_filter :method => :enable_lawful_intercept | ||
</pre> | </pre> | ||
| + | * For more information on Routing Scripts, please see [[Routing script tutorial:Mini Development Guide|mini development guide]] | ||
==Lawful Interception Statistics== | ==Lawful Interception Statistics== | ||
| Line 173: | Line 174: | ||
*** Global | *** Global | ||
*** Per agency | *** Per agency | ||
| − | ** | + | ** Available statistics are |
*** Total / current intercepted calls | *** Total / current intercepted calls | ||
*** Total IRI records generated | *** Total IRI records generated | ||
| Line 181: | Line 182: | ||
*** ... and a few more | *** ... and a few more | ||
| − | == | + | ==IRI records decoding== |
| − | + | As IRI record is encoded in ASN.1 format, some online ASN.1 decoders are also available to check the IRI record. Upload a message/PDU/record file, and the decoded data can be downloaded as a text file in the ASN.1 Value Notation format. | |
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
== References == | == References == | ||
* [http://en.wikipedia.org/wiki/Lawful_interception Wikipedia lawful intercept article] | * [http://en.wikipedia.org/wiki/Lawful_interception Wikipedia lawful intercept article] | ||
| − | * [ | + | * [https://www.etsi.org/deliver/etsi_es/201600_201699/201671/03.02.01_60/es_201671v030201p.pdf ETSI ES 201 671 V3.2.1 (2018-05)] |
| + | * [http://asn1-playground.oss.com/ ASN.1 Playground - learn, play, test] | ||
| + | * [https://www.marben-products.com/asn.1/services/decoder-asn1-security.html Free Online Security ASN.1 Messages Decoder] | ||
| + | * [https://holtstrom.com/michael/tools/asn1decoder.php ASN.1 decoder] | ||
| + | |||
[[category:Tmedia_Features]] | [[category:Tmedia_Features]] | ||
| − | |||
Latest revision as of 05:51, 20 June 2019
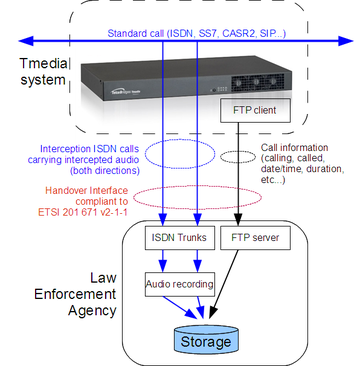
Lawful intercept is a feature provided by service providers to law enforcement agencies (FBI, Interpol, RCMP, etc.) that allows law enforcement agencies to intercept calls by receiving a copy of the audio of both parties and call information records.
Overview
- Lawful Interception (process of intercepting a conversation)
- Interception target (someone under investigation by a law enforcement agency, and for whom the agency wants to intercept the calls)
- Law enforcement agency ( an agency that has, by law, the power to request the interception of calls to or from targets)
- A law enforcement agency sends to the service provider a list of targets to intercept (phone numbers)
- Service provider configures its equipment to intercept the target phone numbers
- When service provider equipment detects a call that involves a target to intercept, it
- Forwards a copy of call audio (both directions) to the agency through forked calls (Content of Communication link (CC link) - a call toward the agency, carrying intercepted audio)
- Sends information records (IRI records) to the agency
- The Telcobridges Lawful Interception implementation is based on specification ETSI ES 201 671 v2.1.1 (2001-09), and not CALEA, PCES, and ANSI T1.678
Lawful Interception Requirements
- Detecting target
- Law enforcement agency provides a list of targets (Type of intercepted targets can be from: PSTN, ISDN, GSM (CS), TETRA, GPRS (PD), UMTS (CS))
- LIID (Lawful Intercept Identifier, unique identifier assigned to a target by an agency) for the target
- Phone number of the target
- Start and end dates and times for the interception
- Service provider updates targets in its equipment and equipment detects a matching calling or called number, and activates the interception
- Law enforcement agency provides a list of targets (Type of intercepted targets can be from: PSTN, ISDN, GSM (CS), TETRA, GPRS (PD), UMTS (CS))
- Intercepting targets
- In a call, each call leg can be an interception target
- When a leg is an interception target, it's intercepted:
- Audio <<from>> this leg is forked to a new outgoing call
- Audio <<to>> this leg is forked to a new outgoing call
- IRI records are generated for this interception
- Intercepting multiple targets
- Both legs may be independently and simultaneously intercepted
- 2 pairs of forked audio outgoing calls
- 2 sets of IRI records
- Both legs may be independently and simultaneously intercepted
Intercepting Audio
- For each direction (audio <<from>> and <<to>> the target):
- A new outgoing call leg is made, toward the agency
- Audio is <<forked>> (half-duplex joined)
- These outgoing call legs are made toward:
- An outgoing NAP explicitly assigned to the agency
- optionally, using specified calling/called numbers
- Forking does NOT require DSPs
- Audio forking is done as soon as possible
- Immediately for the audio <<from>> the target (this may include even the ring back tone, or may include audio from an incoming call during ringing)
- Upon joining with another active leg for the audio <<to>> the target
IRI records
The call data (known as Intercept Related Information or IRI in Europe and Call Data or CD in the US) consists of information about the targeted communications, including destination of a voice call (e.g., called party’s telephone number), source of a call (caller’s phone number), time of the call, duration, and more. Intercept Related Information record (IRI record) is a CDR-style record that contains IRI information on an intercepted call
Types of IRI records
- IRI-BEGIN: Indicates that the interception is starting at first event of the communication attempt, opening the IRI transaction
- IRI-CONTINUE: Indicates call state change at any time during the communication attempt within the IRI transaction
- IRI-END: Indicates the end of the interception at the end of the communication attempt, closing the IRI transaction
- IRI-REPORT: General use for any non-communication related events
For information related to an existing communication case, the record types 1 to 3 shall be used. They form an IRI
transaction for each communication case or communication attempt, which corresponds directly with the communication
phase (set-up, active or release).
For some packet-oriented data services such as GPRS, the first event of a communication attempt is the Packet Data Protocol (PDP)
context activation or a similar event and an IRI-BEGIN record is issued. The end of the communication attempt
shall be the PDP context deactivation or a similar event and an IRI-END record shall be issued. While a PDP context is
active, IRI-CONTINUE records are used for CC relevant IRI data records, IRI-REPORT records otherwise.
Record type 4 is used for non-communication related subscriber action, like Subscriber Controlled Input (SCI) for
service activation. For simple cases, it can also be used for reporting unsuccessful communication attempts.
The record type is an explicit part of the record. The 4 record types are defined independently of target communication
events. The actual indication of one or several communication events, which caused the generation of an IRI record, is
part of further parameters in the record's information content. Consequently, the record types of the IRI
transactions are not related to specific messages of the signalling protocols of a communication case, and are therefore
independent of future enhancements of the intercepted services and of network specific features. Any transport level
information (i.e. higher-level services) on the target communication-state or other target communication related
information is contained in the information content of the IRI records.
For some packet oriented data services such as GPRS, if Lawful Interception (LI) is being activated during an already established PDP context or similar, an IRI-BEGIN record will mark the start of the interception. If LI is being deactivated during an established PDP context or similar, no IRI-END record will be transmitted. The end of interception can be communicated to the LEA a Handover Interface Port 1 (HI1)(for Administrative Information); whereas Handover Interface Port 2 (HI2) transports IRI information and Handover Interface Port 3 (HI3) transports Content of Communication information).
Typical information found in an IRI record
- Record type (Start, Continue, End, Report)
- LIID
- CIN (communication identity number)
- Operator identifier
- Direction (target is originating, or terminating)
- Call state (idle, setup, connected)
- Duration of ring and conversation states
- Calling / called party numbers
- Release reason
- CC link state (setup, active, released, lack of resources)
- CC link release reason
IRI records generating
- IRI records are generated at various states of the interception
- They provide information on the interception, and call state
- In a call, each call leg can be an interception target
- When a leg is an interception target, it's intercepted:
- Audio «from» this leg is forked to a new outgoing call toward the agency
- Audio «to» this leg is forked to a new outgoing call toward the agency
- IRI records are generated for this interception
- Both legs may be independently and simultaneously intercepted
- 2 pairs of forked audio outgoing calls
- 2 sets of IRI records
IRI records encoding
- IRI records are encoded in ASN.1 (a binary encoding standard that is used by IRI records) format and using the basic encoding rules (BER).
- ASN.1 IDs and objects hierarchy for encoding IRI records is provided by ETSI specifications
IRI records values and files specification
- IRI records values can be
- Mandatory in each record
- In one record only for the whole call
- optional (in some records only, or none at all)
- IRI record files can
- Contain only one IRI record (one file per record)
- Contain multiple IRI records (grouped)
IRI records uploading to the agency
- As files, using the FTP protocol
- Telcobridges also supports SFTP as file transfer method
Configuring Lawful Interception
- Configure Lawful Agencies
- Summary of information required
- NAP to use for CC links
- FTP (or SFTP) server info (IP, port, user, password, folder)
- IRI upload mode (per record, grouped)
- Multiple agencies can be configured
- Note: SFTP requires password-less login to be configured (through exchange of keys between servers)
- Summary of information required
- Provide the list of intercepted targets
- The list of intercepted targets is provided as a CSV file
- Uploaded in the <<File DB>> section of the Web Portal
- Required columns:
- liid
- number
- Optional columns
- start
- end
- Example
- The list of intercepted targets is provided as a CSV file
liid,number,start,end John Smith,555-0001,2012-10-24T00:00:00-05:00,2012-10-24T23:59:59-05:00 Joe Dalton,333-3007,2012-01-01T00:00:00-05:00,2012-12-31T23:59:59-05:00 Ben Laden,022-44-66-33-11 Ben Yi,450-621-1990
- Enable Lawful Interception in a Routing Scripts (For Toolpack 2.7)
- The <<lawful interception>> routing script filter is provided with toolpack
- Users only need to <<include>> it in their current routing script
require 'lawful_intercept' (...) include LawfulIntercept (...) after_filter :method => :enable_lawful_intercept
- For more information on Routing Scripts, please see mini development guide
Lawful Interception Statistics
- Live statistics and statistics history
- The Web Portal provides Lawful Interception statistics
- Global
- Per agency
- Available statistics are
- Total / current intercepted calls
- Total IRI records generated
- Total IRI records dropped
- Total failed interceptions
- IRI records upload queue length and state
- ... and a few more
- The Web Portal provides Lawful Interception statistics
IRI records decoding
As IRI record is encoded in ASN.1 format, some online ASN.1 decoders are also available to check the IRI record. Upload a message/PDU/record file, and the decoded data can be downloaded as a text file in the ASN.1 Value Notation format.