|
|
| Line 28: |
Line 28: |
| | | | |
| | Lawful Intercept configuration (NAP to use, login information of the FTP/SFTP server, target numbers to intercept, etc.) can be configured in the [[Toolpack]] Web Portal. | | Lawful Intercept configuration (NAP to use, login information of the FTP/SFTP server, target numbers to intercept, etc.) can be configured in the [[Toolpack]] Web Portal. |
| − |
| |
| − |
| |
| − | ==Required Information from Law Enforcement Agencies==
| |
| − | In order to use Lawful interception in Toolpack, the Law Enforcement Agency must provide:
| |
| − | * List of targets to intercept:
| |
| − | ** Unique target identifier (defined as LIID in ETSI 201 671 v2-1-1)
| |
| − | ** Target phone number
| |
| − | ** Start and end date/time for the interception
| |
| − | * ISDN trunks (or eventually SS7 trunks or SIP path) to carry intercepted call audio
| |
| − | * FTP/SFTP server information:
| |
| − | **Server IP address
| |
| − | **User name
| |
| − | **Password
| |
| − | **Directory path for uploading call information (defined as IRI records in ETSI 201 671 v2-1-1)
| |
| − |
| |
| | | | |
| | == Configuration == | | == Configuration == |
| − | Lawful Interception is configured by the following steps:
| + | *[[Web_Portal_Tutorial_Guide_v2.7#Lawful_Interception|Toolpack v2.7: Lawful Intercept]] |
| − | | + | |
| − | # Configuring a Law Enforcement Agency and it's parameters
| + | |
| − | # Creating a NAP that is connected to the Law Enforcement Agency
| + | |
| − | # Providing a list of targets to intercept (through a coma-separate-values .csv file)
| + | |
| − | # Enabling the Lawful Intercept routing script filter
| + | |
| − | # Exchanging SSH public/private keys with server to allow password-less SFTP
| + | |
| − | | + | |
| − | The configuration of Lawful Interception is described in the [[Web_Portal_Tutorial_Guide_v2.7#Lawful Interception|Lawful Interception]] section of the Web Portal Tutorial guide.
| + | |
| − | | + | |
| − | == Format Lawful Intercept Targets configuration files (.csv) ==
| + | |
| − | The Lawful Intercept Targets configuration files must be formatted in .csv (coma-separated values) format. The following columns must be present:
| + | |
| − | * liid: Text string that uniquely identifies the target to intercept. This ID will be provided with each outgoing call on interception NAP to the Law Enforcement Agency, and in each IRI record uploaded to the FTP/SFTP server.
| + | |
| − | * number: The phone number of the target to intercept. Any call with this number as the calling, or the called number, will be intercepted.
| + | |
| − | * start: (optional) Starting date/time from which the interception can take place. Calls made before that date from/to the target won't be intercepted.
| + | |
| − | * end: (optional) End date/time where this target interception ends. Calls made after that date from/to the target won't be intercepted.
| + | |
| − | | + | |
| − | '''*** Warning: The column names are case sensitive'''
| + | |
| − | | + | |
| − | Example:
| + | |
| − | liid,number,start,end
| + | |
| − | John Smith,5550001,2012-10-24T00:00:00-05:00,2012-10-24T23:59:59-05:00
| + | |
| − | Joe Dalton,14503333007,2012-01-01T00:00:00-05:00,2012-12-31T23:59:59-05:00
| + | |
| − | | + | |
| − | = Enabling the Lawful Intercept routing script filter =
| + | |
| − | Interpretation of the Lawful Intercept Targets configuration files (.csv) is done by a routing script filter, that can easily be added to any existing routing script used by the [[Toolpack]] system.
| + | |
| − | | + | |
| − | Documentation on routing script can be found here: [[Scriptable_Routing_Engine|Scriptable Routing Engine]]
| + | |
| − | | + | |
| − | == Installing ruby 'gem' ==
| + | |
| − | The Lawful Intercept filter script requires the 'json' ruby gem.
| + | |
| − | TMedia units ([[TMG800]], [[TMG3200]], [[TMG7800]]) provided by TelcoBridges are now shipped with that 'gem' already installed.
| + | |
| − | | + | |
| − | If you have an older TMedia, or if you are using your own host, please validate that the host has the 'json' gem already installed:
| + | |
| − | gem list --local
| + | |
| − | | + | |
| − | In case it's missing, you can install it from a shell:
| + | |
| − | gem install json
| + | |
| − | | + | |
| − | == Including the Lawful Intercept filter script ==
| + | |
| − | The Lawful Intercept filter is activated by:
| + | |
| − | * Including the 'Lawful intercept' module in your routing script: '''''require 'base_routing''''''
| + | |
| − | * Include the LawfulIntercept class: '''''include LawfulIntercept'''''
| + | |
| − | * Add the Lawful Intercept "after_filter" to your script: '''''after_filter :method => :enable_lawful_intercept'''''
| + | |
| − | | + | |
| − | == Example script ==
| + | |
| − | Here is an example "simple routing" script that enables Lawful Intercept:
| + | |
| − | | + | |
| − | require 'base_routing'
| + | |
| − |
| + | |
| − | # Insert following line ===================>
| + | |
| − | require 'lawful_intercept'
| + | |
| − |
| + | |
| − | class SimpleRouting < BaseRouting
| + | |
| − | # Insert following line ===================>
| + | |
| − | include LawfulIntercept
| + | |
| − |
| + | |
| − | route_match :call_field_name => :called
| + | |
| − | route_match :call_field_name => :calling
| + | |
| − | route_match :call_field_name => :nap
| + | |
| − | route_remap :call_field_name => :called, :route_field_name => :remapped_called
| + | |
| − | route_remap :call_field_name => :calling, :route_field_name => :remapped_calling
| + | |
| − | route_remap :call_field_name => :nap, :route_field_name => :remapped_nap
| + | |
| − |
| + | |
| − | # Insert following line ===================>
| + | |
| − | after_filter :method => :enable_lawful_intercept
| + | |
| − | end
| + | |
| − |
| + | |
| − | @@routing = SimpleRouting.new
| + | |
| − |
| + | |
| − | def init_routes( routes )
| + | |
| − | @@routing.init routes
| + | |
| − | end
| + | |
| − |
| + | |
| − | def route( call, nap_list )
| + | |
| − | @@routing.route call, nap_list
| + | |
| − | end
| + | |
| − | | + | |
| − | = Allowing SFTP password-less connection =
| + | |
| − | Toolpack can use the secure FTP (SFTP) protocol to upload IRI records to a remote server.
| + | |
| − | | + | |
| − | Please read the following documentation:
| + | |
| − | *[[configuring_lawful_interception_ssh|Configure IRI (Intercept Related Information) records for SFTP upload]]
| + | |
| | | | |
| | == References == | | == References == |
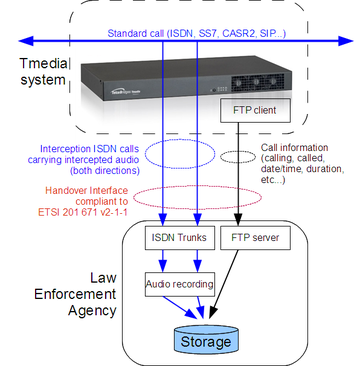
Lawful interception will identify a call to intercept, and send the following information to one or multiple Law Enforcement agencies:
A call that matches the number and the time period will be intercepted.
A call that matches the number (calling or called number) and the time period will be intercepted.
In addition, information records (containing general call information like calling/called number, timestamps, and call duration, etc.) will be sent to the Law Enforcement Agency. That information is sent as data files (format specified by ETSI 201 671 v2-1-1) to a FTP server (Toolpack also supports SFTP for more security).
Lawful Intercept configuration (NAP to use, login information of the FTP/SFTP server, target numbers to intercept, etc.) can be configured in the Toolpack Web Portal.