Toolpack:Tsbc TLS Profiles
(→Upload local certificates (optional)) |
|||
| Line 31: | Line 31: | ||
== Upload local certificates (optional) == | == Upload local certificates (optional) == | ||
| − | Toolpack already contains a unique | + | Toolpack already contains, by default, a unique self-signed certificate (unique per Toolpack system, shared for 1+1 hosts). This certificate is used for HTTPs, and can also be used for TLS. |
| − | In case you want to use a custom local certificate, proceed as follows: | + | In case you want to use a custom local certificate (like an officially signed certificate for your domain name), proceed as follows: |
* Repeat the same procedure as above (but using "Local" certificate type) to import the local certificate | * Repeat the same procedure as above (but using "Local" certificate type) to import the local certificate | ||
* Use ssh (command-line or using tool like Filezilla) to upload the private key to the unit to following path. Use the '''same file''' name as the local certificate name previously used to import in the web portal (except file extension): | * Use ssh (command-line or using tool like Filezilla) to upload the private key to the unit to following path. Use the '''same file''' name as the local certificate name previously used to import in the web portal (except file extension): | ||
Revision as of 13:26, 11 March 2019
Certificates are used to provide secure connections, like HTTPs (secure connection to thw web portal) or secure SIP calls (SIP over TLS). This pages describes how to import certificates and group them into TLS profiles.
These TLS profiles can later be used to create SIP Transport servers using TLS.
Contents |
Configuring Certificates and TLS Profiles
Applies to version(s): v3.1 and above
Multiple TLS profiles can be created in Toolpack. A TLS profile is a collection of certificates and other settings that define the behavior of TLS connections. Multiple TLS profiles can be used to expose different certificates and options to different TLS connections in Toolpack, though one TLS profile is generally enough.
Upload trusted certificates
Click Create New Certificate
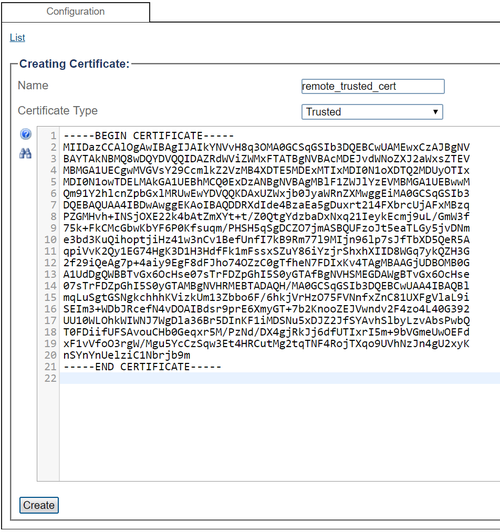
Configure certificate parameters
- Give a name that is meaningful to you
- Select "Trusted" certificate to import a remote party's certificate to trust
- Drag-and-drop (or copy-paste) the certificate's text content into the appropriate text box
- Click "Create"
Upload local certificates (optional)
Toolpack already contains, by default, a unique self-signed certificate (unique per Toolpack system, shared for 1+1 hosts). This certificate is used for HTTPs, and can also be used for TLS.
In case you want to use a custom local certificate (like an officially signed certificate for your domain name), proceed as follows:
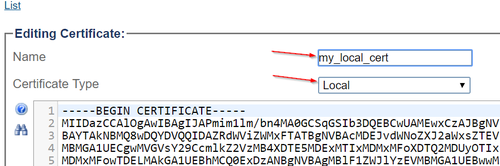
- Repeat the same procedure as above (but using "Local" certificate type) to import the local certificate
- Use ssh (command-line or using tool like Filezilla) to upload the private key to the unit to following path. Use the same file name as the local certificate name previously used to import in the web portal (except file extension):
/lib/tb/toolpack/pkg/ssl_certificate/
Example:
Then:
scp my_local_cert.key root@MyFreeSbcHostName:/lib/tb/toolpack/pkg/ssl_certificate/
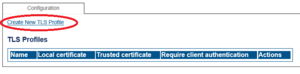
Create TLS profile
Click Create New TLS Profile
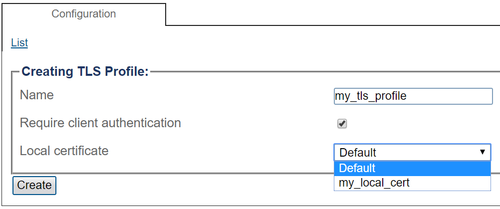
Configure TLS Profile parameters
- Give a name that is meaningful to you
- Decide if client authentication is required (meaning that incoming connections require remote side to present a trusted certificate)
- Select a local certificate (either one imported earlier, or the "Default" certificate which is automatically generated by Toolpack and is also used for HTTPS)
- Click "Create"
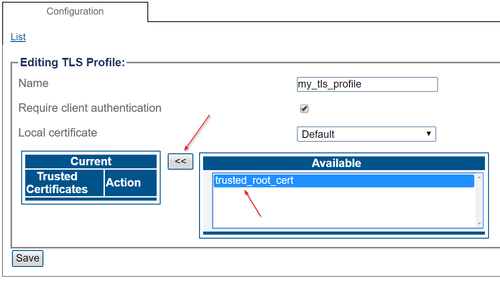
- Select one or multiple "trusted" certificates, which correspond to remote equipment's certificates (or root certificates from which remote certificates are signed)