Toolpack:Create Sbc Access Rule A
(→List of Parameters) |
(→List of Parameters) |
||
| Line 165: | Line 165: | ||
* [[Parameter: SBC Filter Source Netmask|Source Netmask]] | * [[Parameter: SBC Filter Source Netmask|Source Netmask]] | ||
* [[Parameter: SBC Filter Source Port|Source Port]] | * [[Parameter: SBC Filter Source Port|Source Port]] | ||
| − | * [[Parameter: SBC Filter Destination | + | * [[Parameter: SBC Filter Destination IP|Destination IP]] |
* [[Parameter: SBC Filter Destination Netmask|Destination Netmask]] | * [[Parameter: SBC Filter Destination Netmask|Destination Netmask]] | ||
* [[Parameter: SBC Filter Destination Port|Destination Port]] | * [[Parameter: SBC Filter Destination Port|Destination Port]] | ||
* [[Parameter: SBC Filter Override Default Thresholds|Override Default Thresholds]] | * [[Parameter: SBC Filter Override Default Thresholds|Override Default Thresholds]] | ||
<br> | <br> | ||
Revision as of 17:01, 4 October 2016
Applies to version(s): v2.10
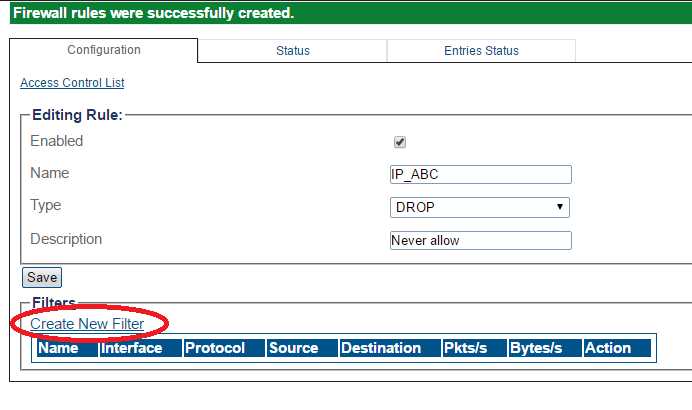
Firewall Rules
In addition to the default access rules that are included with the SBC, one or more custom rules can be created and their priority in a series of rules can be set. To add a new rule or to change its priority, do the following:
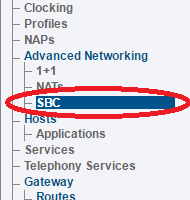
1-Click SBC in the navigation panel.
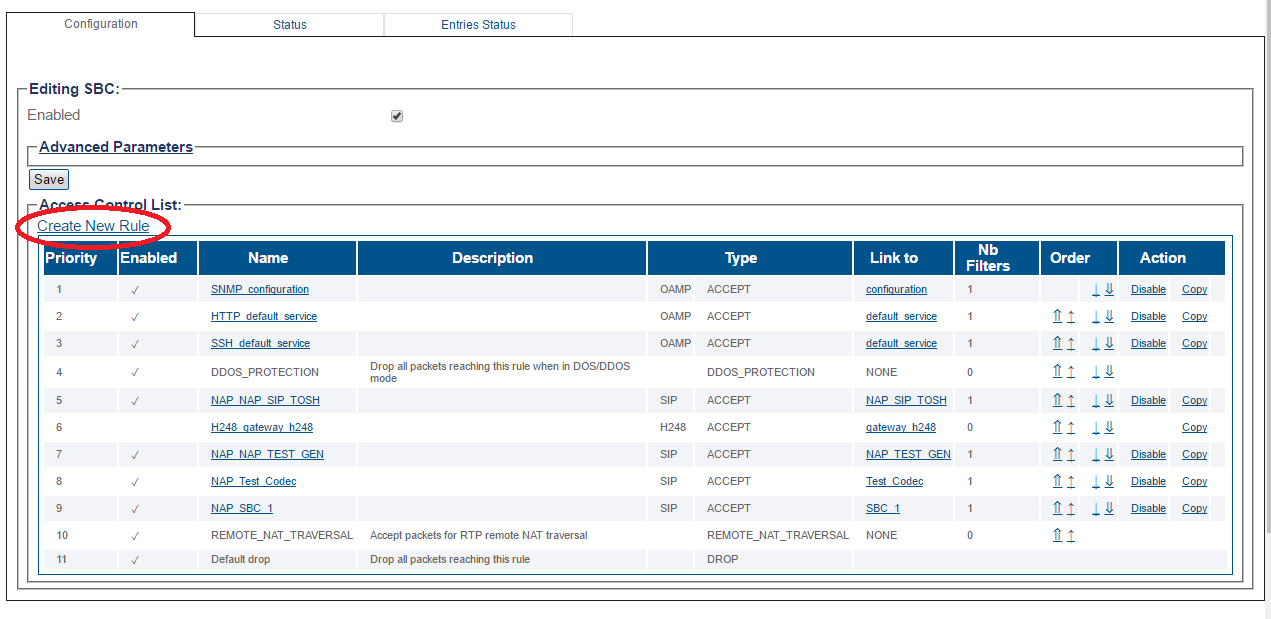
2-Click Create New Rule.
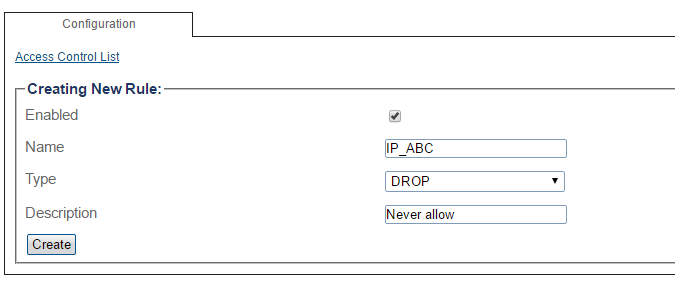
3-Enter values for the rule.
- Click Create
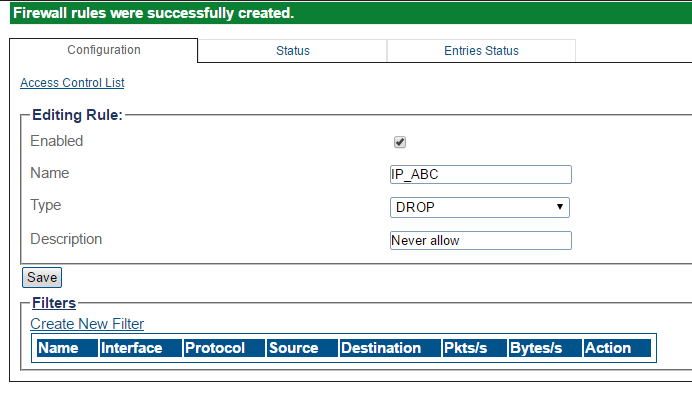
4-Verify that Firewall rules were successfully created message is displayed.
Firewall Filters
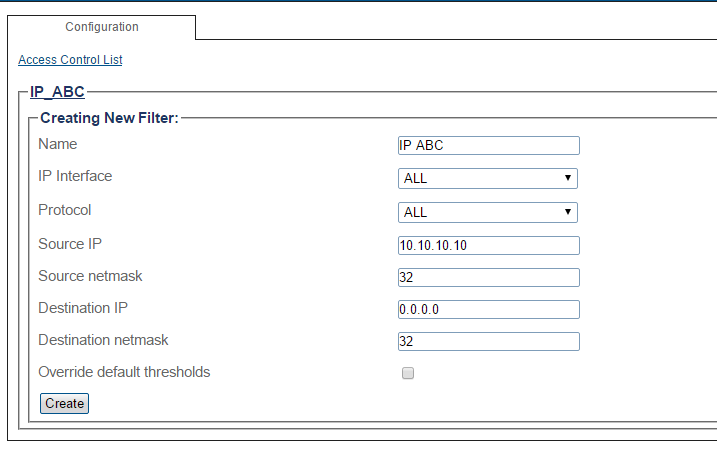
To customize the actions of a firewall rule, you can add one or more filters to the rule.
1-To define what the rule will do, click Create New Filter.
2-Enter values for the filter.
- Click Create
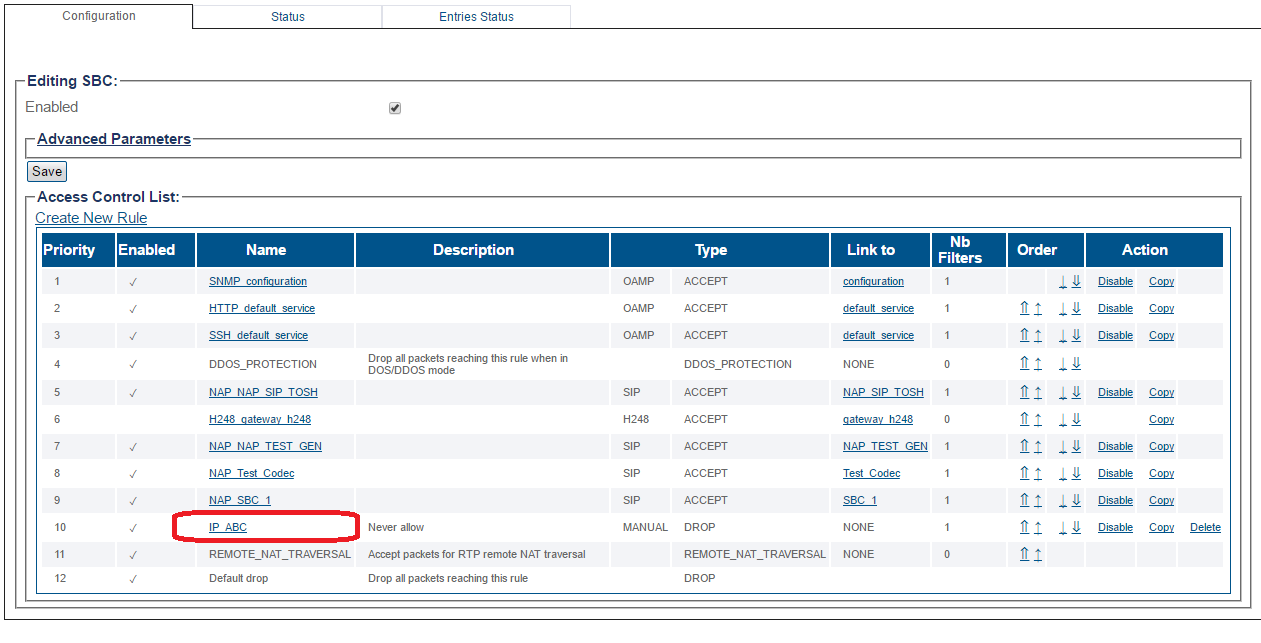
To change the priority of an access rule, use the arrow icons.
- To increase the priority of an access rule, use either the double or single arrow
 to move the rule up by one position, or to the top of the list.
to move the rule up by one position, or to the top of the list.
- To decrease the priority of an access rule, use either the double or single arrow
 to move the rule down by one position, or to the bottom of the list.
to move the rule down by one position, or to the bottom of the list.
Position of sample rule before it is moved
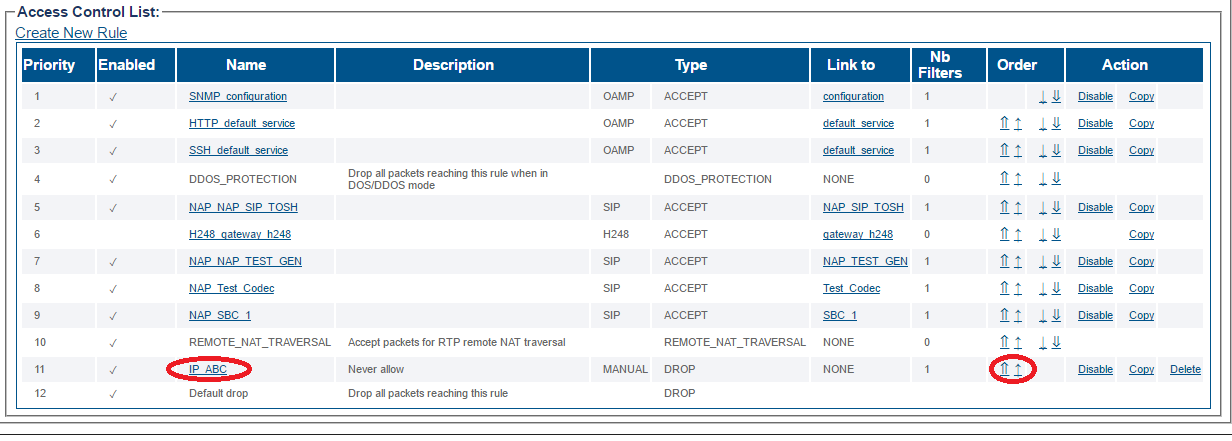
Position of sample rule after it is moved
Firewall Rule
Path
/configurations/@[configuration_name]/firewalls/firewall/rules/@[firewall_rule]
Parameters (text)
/configurations/@[configuration_name]/firewalls/firewall/rules/@[firewall_rule] automatic = true description = "Drop all packets reaching this rule when in DOS/DDOS mode" enabled = true firewall_entry_type = "DDOS_PROTECTION" name = "DDOS_PROTECTION" priority = 4 /configurations/@[configuration_name]/firewalls/firewall/rules/@[firewall_rule]/filters
Parameters (json)
Firewall Rule
{
"automatic" : true,
"description" : "Drop all packets reaching this rule when in DOS/DDOS mode",
"enabled" : true,
"firewall_entry_type" : "DDOS_PROTECTION",
"name" : "@[firewall_rule]",
"priority" : 4,
"filters" : {
}
}
Firewall Filter
Path
/configurations/@[configuration_name]/firewalls/firewall/rules/@[firewall_rule]]/filters/@[firewall_filter]
Parameters (text)
/configurations/@[configuration_name]/firewalls/firewall/rules/@[firewall_rule]/filters/@[firewall_filter] custom_protocol = 0 destination_ip = "0.0.0.0" destination_netmask = "32" destination_port = "161" entry_duration = "15 minutes" ip_interface = "" maximum_bandwidth = "0 Bps" maximum_bandwidth_packets = "0 pps" name = "@[firewall_filter]" override_default_thresholds = false protocol = "UDP" source_ip = "0.0.0.0" source_netmask = "32" source_port = "0" temporary_ban_duration = "5 minutes"
Parameters (json)
Firewall Rule
{
"custom_protocol" : 0,
"destination_ip" : "0.0.0.0",
"destination_netmask" : "32",
"destination_port" : "161",
"entry_duration" : "15 minutes",
"ip_interface" : "",
"maximum_bandwidth" : "0 Bps",
"maximum_bandwidth_packets" : "0 pps",
"name" : "@[firewall_filter]",
"override_default_thresholds" : false,
"protocol" : "UDP",
"source_ip" : "0.0.0.0",
"source_netmask" : "32",
"source_port" : "0",
"temporary_ban_duration" : "5 minutes"
}
List of Parameters
SBC Rule
SBC Filter
- Name
- IP Interface
- Protocol
- Source IP
- Source Netmask
- Source Port
- Destination IP
- Destination Netmask
- Destination Port
- Override Default Thresholds